Our approach to cyber security
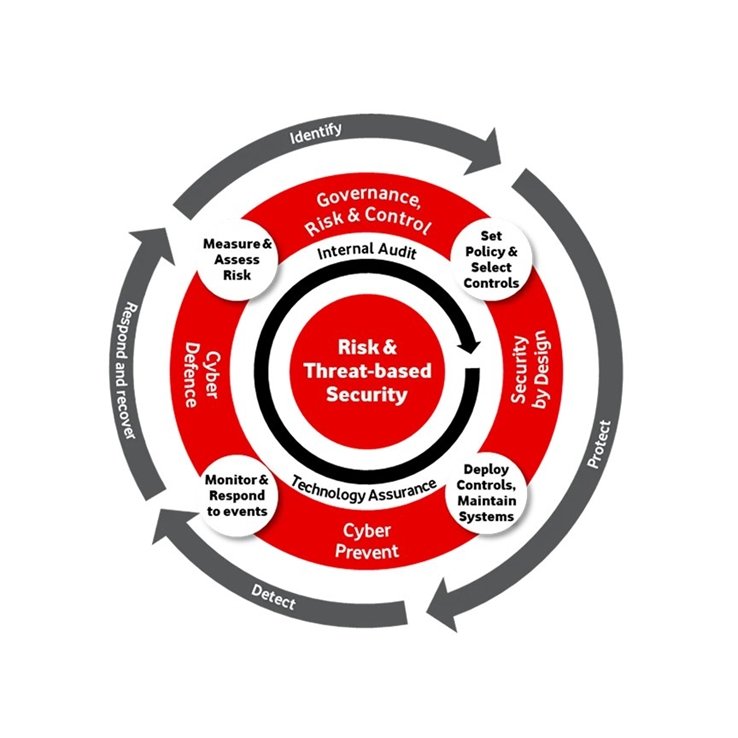
Our globally consistent cyber security operating model is based on leading industry security standards published by the US National Institute of Standards and Technology. The model is designed to reduce risk by constantly identifying threats, defending, responding and continuously improving security.
We operate cyber capabilities with an in-house international team of over 900 employees. Our scale means we benefit from global collaboration, technology sharing, deep expertise and greater visibility of emerging threats. Our global security operations take inputs and telemetry from all the markets where we operate. We augment internal capabilities with third party specialist technical expertise where necessary, such as digital forensics, red teaming and penetration testing, and use specialist resources to test our telecommunications networks.

Our strategy
Our vision is a secure connected future for customers and society. We are motivated by a clear purpose to inspire customer trust and loyalty through providing sustained cyber security and cyber resiliency, ultimately contributing to a secure society and an inclusive future for all.
Our cyber security strategy supports our vision and goals, and forms part of our wider business strategy. We regularly define and communicate updated priorities so all business areas are clear on our security investment priorities.
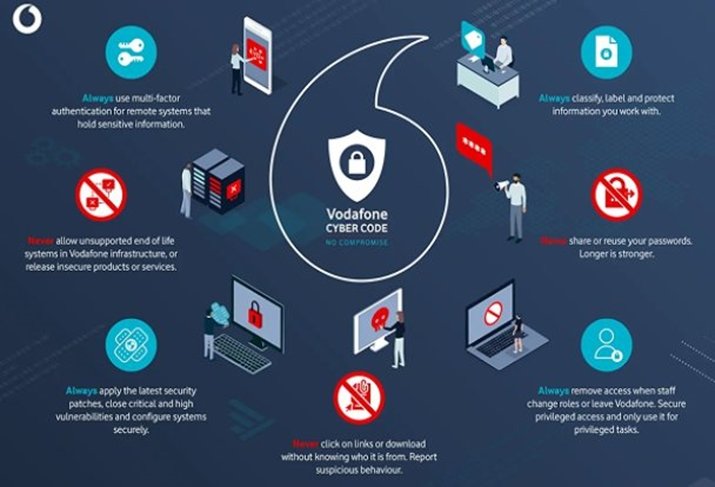
Our cyber code
Every employee has responsibility for cyber security. The Vodafone Cyber Code has been designed to simplify and explain basic security controls and procedures to all employees. The Cyber Code is embedded in our Code of Conduct and is the foundation of how we expect all employees to behave for best practice in cyber security. It consists of seven areas where employees must follow good security practice.
Risks and controls

The challenge
Risk management is fundamental to maintaining the security of our services across every aspect of our business. We dedicate significant resources to managing cyber security risk, which we separate into three main areas: internal, external and supply chain.
We conduct regular reviews of the most significant security risks affecting our business and develop strategies and policies to detect, prevent and respond to them. Our cyber security strategy focuses on minimising the risk of cyber incidents that affect our networks and services. When incidents do occur, we aim to identify the root causes and use them to improve our controls and procedures.

Our risk and control framework
Risk management is fundamental to maintaining the security of our services across every aspect of our business. We dedicate significant resources to managing cyber security risk, which we separate into three main areas: internal, external and supply chain. Most risks and threats are prevented from occurring and we expect most will be detected before they cause harm and need a response.
We have a common global methodology for cyber security risk management. By mapping threats and specific attack techniques to the controls that most significantly reduce risk, this allows gaps to be highlighted.
We have set targets for key controls to be effective, meaning they are well-implemented and cover the relevant systems. New targets are set each year. Our control framework evolves based on the threat landscape, technology changes, our strategic and business priorities, and changing regulation.

Threats and incidents
An important part of our operating model is to gather intelligence and insights about threats. We actively engage with stakeholders across industry, with regulators, standard-setting bodies and governments. Collaboration is vital to respond to threats, protect our organisation and workforce, and build safe online and digital spaces for customers and society.
As a global connectivity provider, we see a range of cyber threats. We use our layers of controls to try to identify, block and mitigate threats and reduce business or customer impact. Our global security operations capability handles billions of events and logs from sensors across our footprint, detecting potential threats and events.
We classify security incidents on a scale according to severity, measured by potential business and customer impact. In the event of a cyber breach, disclosure is made to the relevant authorities in line with local and global regulations and laws and a risk assessment considering the impact on customers. We complete post-incident reviews to learn the lessons from incidents and any improvements needed.